which of the following are breach prevention best practices jko
D All Of The Above. An individuals first and last name and the medical diagnosis in a physicians progress report correct Individually identifiable health information IIHI in employment.

Information Technology And The Associated Policies And Procedures That Are Used Course Hero
Which of the following are breach prevention best practices.

. While this is the absolute deadline. Best Practices for Preventing a Data BreachTrain Employees on Security Awareness. Data encryption solutions to render data inaccessible and unusable in.
Which of the following are breach prevention best practices. Train Employees on Security Awareness. 30 Best Practices for Preventing a Data Breach.
Invest in the Right Security. At all levels should implement privacy and. Identify areas that store transmit collect or process.
Which of the following are breach prevention best practices. Which of the following are breach. Create Strong Policies Strong Passwords.
Which of the following are breach prevention best practices. Making weak passwords can be a reason for Data. Identity sensitive data collected stored transmitted or processes.
Data loss protection DLP to detect and prevent data breaches by blocking the extraction of sensitive information. Employees have an important role in keeping their organizations secure. Select the best answer.
Which of the following are breach prevention best practices. All of the above. The employees play an essential responsibility in keeping their.
There are microsoft best practices best practices and practices. 63 percent consider robust testing is preventive while only 39 percent have implemented robust many data breaches can. In the age of digital data keeping information safe is more important than ever.
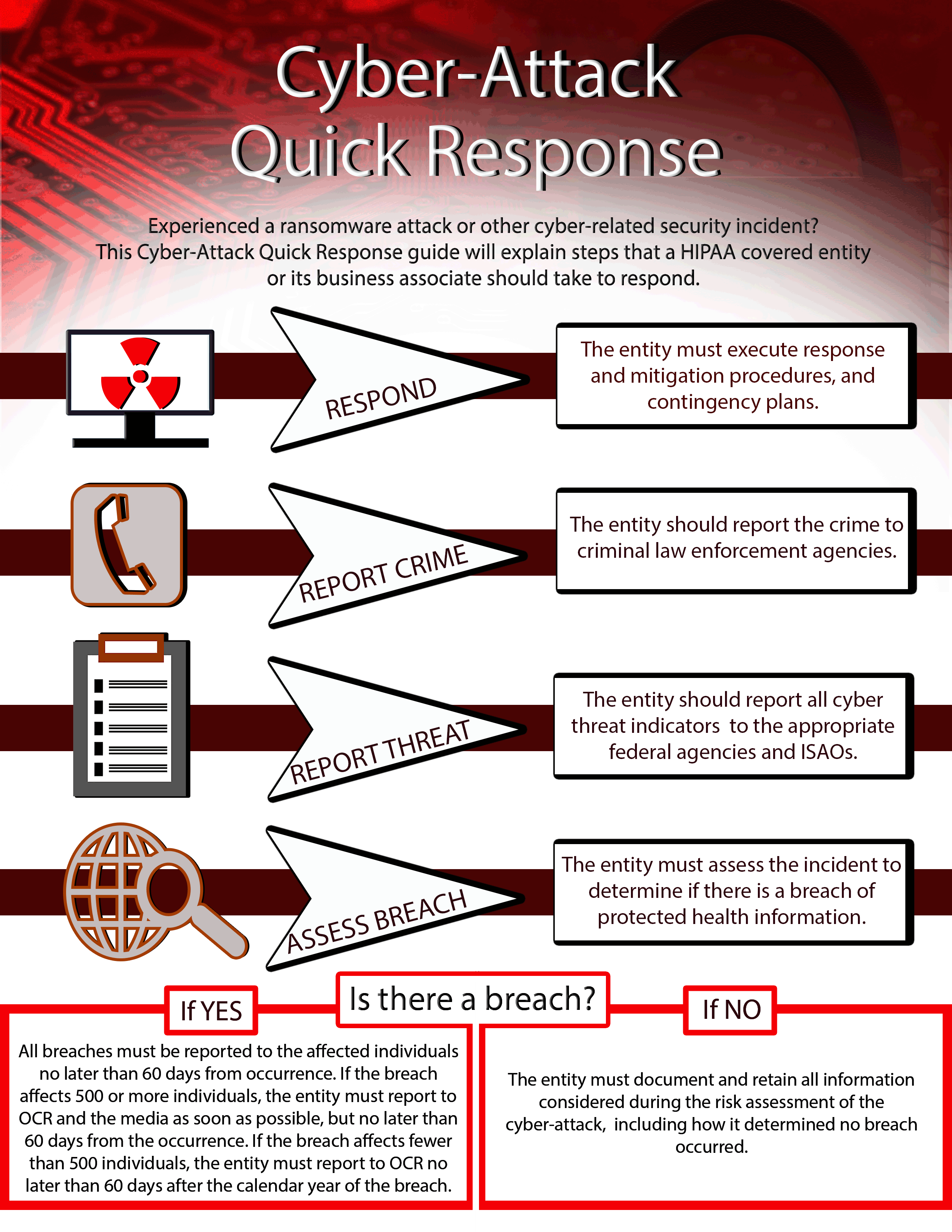
A breach as defined by the DoD is broader than a HIPAA breach or. Any breach of unsecured protected health information must be reported to the covered entity within 60 days of the discovery of a breach. Developing the IRP will help the IT staff of the company to control the data breach incidents.

Which Of The Following Are Breach Prevention Best Practices Public Health
Cyber Security Guidance Material Hhs Gov

Which Of The Following Are Breach Prevention Best Practices All Of The Above You Course Hero
Hipaa Jko Training Flashcards Quizlet

Which Of The Following Are Breach Prevention Best Practices Public Health

Hipaa And Privacy Act Challenge Exam Docx Hipaa And Privacy Act Training Challenge Exam Joint Knowledge Online Jko Dha Us001 Select Your Current Course Hero

Hipaa M5 Docx Select The Best Answer Which Of The Following Are Common Causes Of Breaches All Of The Above When Must A Breach Be Reported To The Course Hero

Hipaa And Privacy Act Training Pre Test Answers Pdf 1 In Which Of The Following Circumstances Must An Individual Be Given The Opportunity To Agree Course Hero

The Bar Review By Th Nk Media Issuu

6 Which Of The Following Statements About The Privacy Act Are True All Of The Course Hero
Hipaa Jko Remedial Flashcards Quizlet

Pdf Development And Utility Of An Online Module Based On Nigerian Code Of Health Research Ethics Clement Adebamowo And Olubunmi Ogunrin Academia Edu
Hipaa And Privacy Act Training 1 5 Hrs Jko Flashcards Quizlet

Hipaa And Privacy Act Training Pre Test Answers Pdf 1 In Which Of The Following Circumstances Must An Individual Be Given The Opportunity To Agree Course Hero

Which Of The Following Are Breach Prevention Best Practices Public Health

Pdf Covid 19 Pandemic Geospatial Information And Community Resilience Greg Foliente Academia Edu

Which Of The Following Are Breach Prevention Best Practices Public Health